How Do I Identify My Critical Applications?
Critical applications are essential for business continuity. If a business-critical application fails, your organization cannot operate normally, leading to financial losses, decreased productivity and loss of customer trust.
It’s important for you to be able to identify your critical applications so we can help you implement security measures and prioritize them based on importance in the event of a data breach.
Categories of Critical Applications
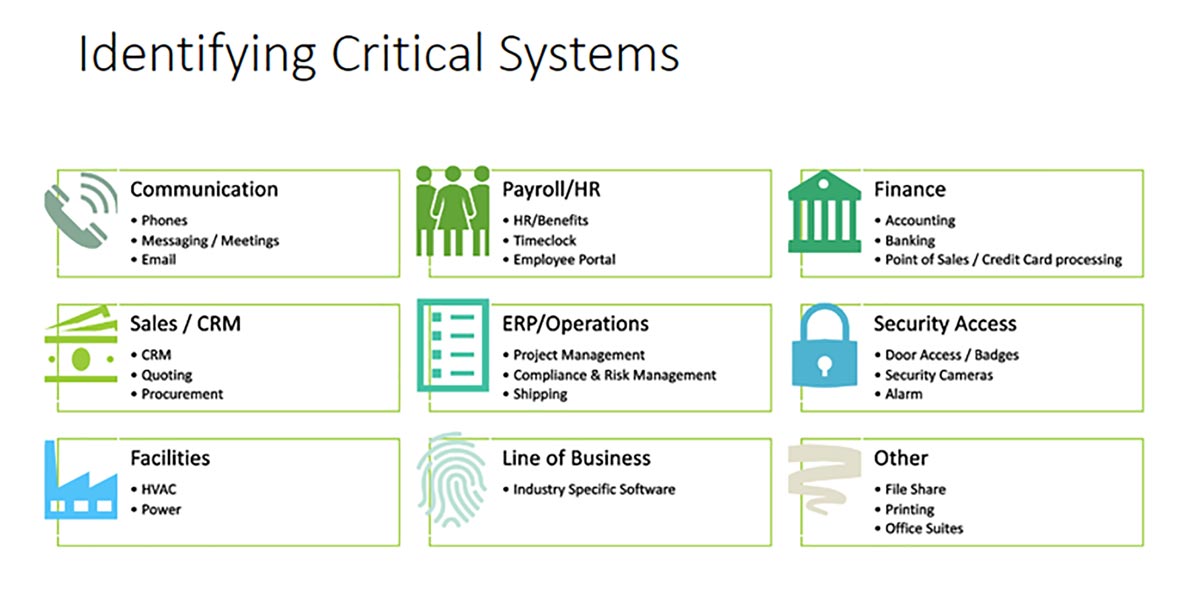
Your critical applications probably will fall under one of the nine categories, as outlined below. This isn’t an exhaustive list but rather a starting point to get you thinking about your critical applications.
Your organization or industry could have unique critical systems that are not listed.
What Should Be Documented About Each Application?
Now that you’ve identified your critical applications, it’s important to document five key attributes for each. Below the definitions, you’ll see a mockup of what a critical application table might look like.
- Name: Name of the application
- Service Location: Whether the application is located on the cloud, an on-premises server or an on-premises workstation
- Importance: Critical, high or low (Note: we don’t have a precise definition for importance. Think about things like, what would we do if this stopped working? How long would it need to be unavailable before we started feeling operational pain? How long before we would start feeling financial impact? How long could this application be expected to be down before you’d start sending employees home?)
- Application Champion: An employee on your team who is responsible for this or knows the most about it
- Number of Users: How many employees use this application?
- Description: What does this application do?
Name | Service Location | Importance | Champion | # Users | Description |
PhoenixPM | Cloud (SaaS) | Critical | Alex Johnson | 15 | Project management tool |
SkyCRM | Cloud (SaaS) | High | Maria Gonzalez | 20 | Customer relationship management software |
LedgerLink | On-premises | Medium | James Park | 5 | Financial management software for accounting, invoicing, payroll and reporting |
TeamConnect | Cloud (SaaS) | High | Samantha Wei | 25 | Unified communication platform offering chat, video calls, etc. |
SecureGate VPN | On-premises | Critical | Michael Thompson | 25 | VPN service for secure remote access |
Insight Analytics | Cloud (SaaS) | Medium | Ethan Lee | 8 | Business intelligence tool that offers data visualization, reporting and analytics |
ConnectMail | Cloud (SaaS) | High | Natalie Kim | 20 | Email hosting service |
ShippingWorld | On-premises (Workstation) | High | Natalie Kim | 20 | Specialized shipping application |
Why Should Critical Applications Be Documented?
We ask for an inventory of your critical applications for several reasons:
- Understanding business needs: By knowing the critical applications, we can better understand your organization’s processes and needs. This helps us make well-informed decisions regarding your .
- Risk assessment: An inventory of critical applications allows us to assess potential risks, such as security vulnerabilities or compatibility issues with other software or hardware.
- Disaster recovery planning: In the event of a disaster, such as a system failure or cyberattack, having an inventory of critical applications is essential for planning recovery strategies and ensuring business continuity.
- Maintenance and upgrades: A critical applications list helps us plan for regular maintenance, updates and upgrades without disrupting important business operations.
- Budgeting and resource allocation: An inventory helps us allocate resources more effectively, ensuring that critical applications have the necessary funding and infrastructure support.
In essence, an inventory of critical applications helps us manage, protect and optimize these applications to support your organization effectively.
Managed IT Services in West Michigan
Looking to keep your business running smoothly while increasing productivity, security and profitability? Contact us here for all your information technology needs.











