What Do We Audit for in Our Advisory Alignment Process?
Our proactively ensure your IT environment runs smoothly.
Many people think IT is a “set it and forget it” deal, but it’s more like maintaining a garden. Just as a garden requires ongoing care to ensure everything grows and thrives, your IT environment needs regular attention and updates to remain secure and efficient.
While part of our job is reacting to broken things, there are times when we need to be proactive about your IT environment. It’s always more cost-effective to address things before they become an emergency.
Our advisory alignment audits happen monthly — for things that are likely to need attention on a regular 30-day basis — as well as annually — for things that can be assessed yearly.
What Do We Check for Monthly?
Each month, we focus on three critical areas to keep your IT environment secure and efficient:
- Active Directory
- Do all users have only the permissions they need? Having too many privileged accounts is like having too many master keys to your network.
- Are there any inactive user accounts that need to be removed? We look to catch forgotten user accounts more than 30 days old. A stale user in your active directory opens your organization up to potential security issues, especially if the employee was terminated.
- Microsoft 365
- Are all admin accounts protected with multifactor authentication? Admin accounts should be treated with extra scrutiny because they can change security settings, install and uninstall software, and make changes to other accounts. MFA should be enforced anywhere they exist.
- Are any mailboxes approaching their size limit? We warn employees and help them avoid email disruptions caused by a mailbox size limit. Microsoft sends warnings to users, but they often get ignored.
- Is there any unauthorized access from abroad? We want to ensure there is no unauthorized foreign access to Microsoft 365 accounts, especially overseas. We block access to Microsoft 365 accounts when employees are traveling out of the country unless they give us advance notice.
- Backups
- Is your backup schedule still meeting your business needs? As your data grows and business needs change, the schedule frequency for backups also might change.
- Are we backing up everything that needs to be backed up? We want to ensure we are adequately backing up all the files, documents and data that need to be preserved to keep your business running during an incident.
“By regularly auditing your infrastructure, you can reduce unexpected costs and downtime so you and your employees remain productive.”
What Do We Check for Annually?
Annually, we conduct a comprehensive review to ensure long-term stability and security.
- Physical Server Health Check
- Are our servers functioning properly and up to date?
- We assess the hardware and software status of your servers to ensure they are functioning properly. This includes verifying that firmware and drivers are up to date and performing stress tests to identify potential failures.
- Microsoft Secure Score
- How well are we aligning with best security practices?
- Microsoft Secure Score is a tool designed to help organizations assess and improve their cybersecurity posture. It provides a numerical score based on security settings and how well you’re aligning with best security practices.
- Virtual Server Role/Configuration
- Are our virtual servers properly documented and optimized?
- This includes defining the roles each virtual machine will play (application server, domain controller, print server, etc.) and configuring network settings, operating systems and software applications.
- Internet & Hosting
- Do we have the bandwidth necessary for seamless access to resources?
- This includes checking bandwidth but also security.
- Single Points of Failure
- Have we documented and identified areas for improvement?
- We identify single points of failure and suggest cost-effective redundancy measures to enhance reliability, tailored to each client’s needs and budget.
- Security Catchall
- Are our security measures and practices up to date?
- This includes policies, procedures, tools and technologies designed to protect you from various threats, ensuring overall security hygiene.
- Network Segmentation (VLANs)
- Is our network segmented to contain potential breaches and aligned with our complexity tolerance?
- We identify areas for improvement while balancing the benefits of segmentation with the complexity it introduces, ensuring the solution fits each client’s specific needs.
- Active Directory, Access and Permissions
- Does every user have the correct access and permissions?
- Pertains to the management of user identities, authentication and authorization within an IT environment. We confirm every user has the correct access and permissions, and create new groups if necessary.
- Firewall Configuration
- Are our firewall rules and policies regularly updated?
- We want to ensure rules and policies are regularly monitored to control incoming and outgoing network traffic. We’ll update access control lists, configure ports and check intrusion detection and prevention systems.
- Wireless Access
- Is our wireless network secure and reliable?
- Your organization probably relies on a reliable and secure wireless connection for your employees. This includes managing wireless access points and configuring security protocols.
- Network Configuration
- Is our network configured for efficient and secure communication?
- The configuration and management of network devices and settings to ensure efficient and secure communication within an IT infrastructure.
- Critical Applications
- Are our critical applications available, performant and secure?
- Critical applications are software applications that are vital for the operation of an organization’s core business functions. They are essential for business continuity, so it’s important they are monitored regularly to ensure their availability, performance and security.
What Do the Results Show?
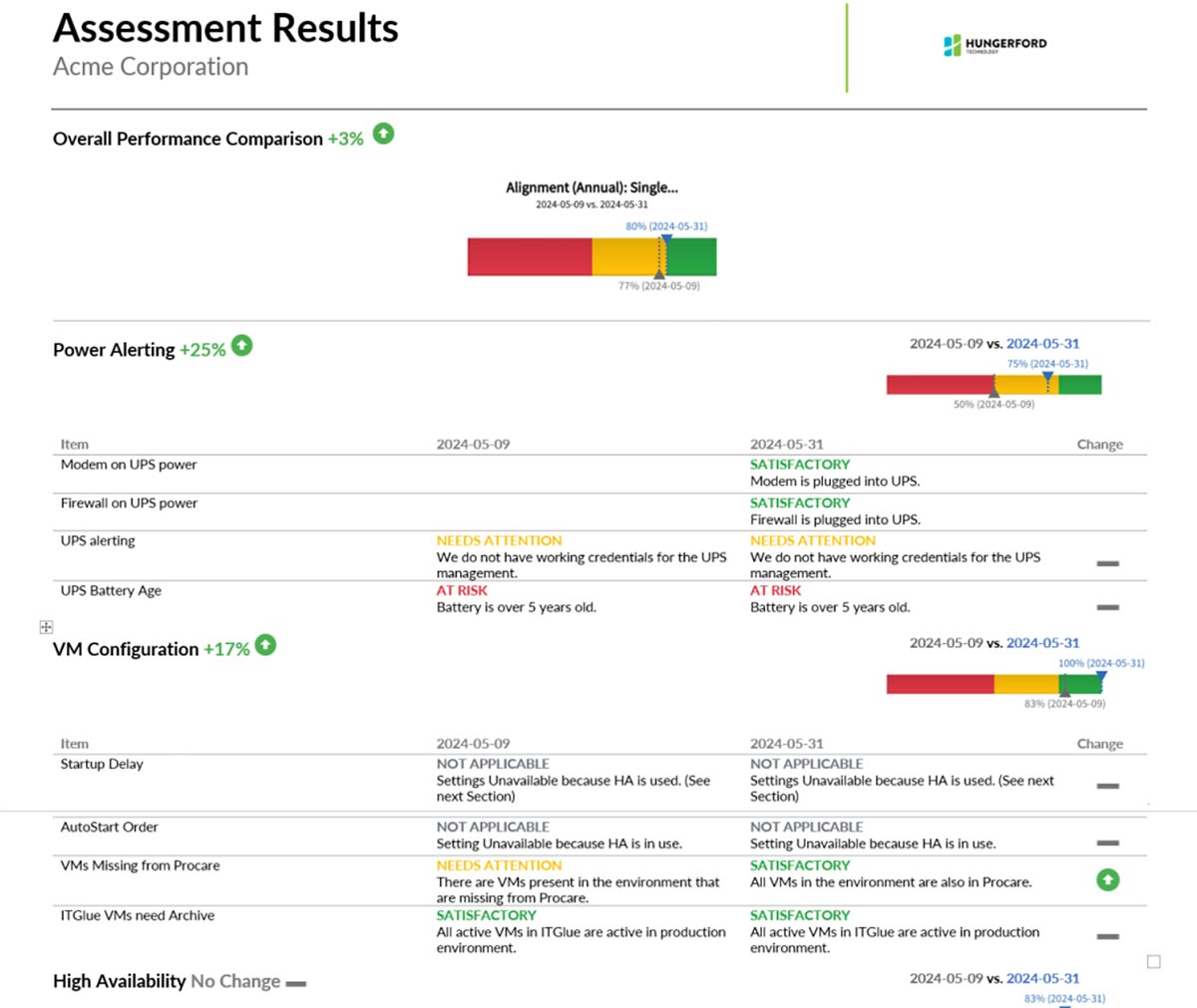
Here’s a sample of the results we provide to our advisory clients.
Green indicates satisfactory performance, yellow highlights areas needing attention and red signals items at risk.
This visual representation helps you quickly understand your IT environment’s status and track improvements over time.
By regularly auditing your infrastructure, you can reduce unexpected costs and downtime so you and your employees remain productive.
Interested in Our Advisory Services?
If you want to learn more about our advisory services, contact us here to find out how we can help keep your business running smoothly while increasing productivity, security and profitability.
Did you like this blog? You can subscribe to our newsletter to receive a weekly email with our latest blog posts.











