What Happens When You Use the Phish Alert Button?
Editor’s note: In recognition of this October, we are publishing a series of blog posts dedicated to educating and informing you about cybersecurity practices. This is the 13th in a series of posts. Below, you can find a list of links to the rest of the series:
- What is a Pig Butchering Scam and How Do You Protect Yourself?
- 6 Conditional Access Policies You Should Turn on Now
- Tips for Running an Effective Cybersecurity Awareness Campaign
- What is Quishing and How Do You Protect Yourself?
- Early Warning Signs Your Employees Need to Look Out for and Report to IT
- My Dad Lost Thousands of Dollars in a Romance Scam. Here’s How They Work and How to Protect Yourself
- NIST Releases New Password Rules: What Does It Mean for You?
- 7 Reasons Your Organization Needs Cybersecurity Insurance
- Why Does My Organization Need Cybersecurity Insurance and an MSP?
- Top 3 Cybersecurity Threats We Uncovered at GrrCon 2024
- Why Keeping a File with Passwords on Your Computer is a Terrible Idea
- How Do Passwords Get Hacked?
- Why Does Social Engineering Happen?
We’ve previously discussed what you should do when you get a suspicious-looking email and why using the phish alert button is important.
But what happens after you report an email?
Reporting an email starts a chain of events that helps us identify potential threats through the automated process of rules, tags and actions. If a threat is identified, we can remove the threat from all users’ inboxes.
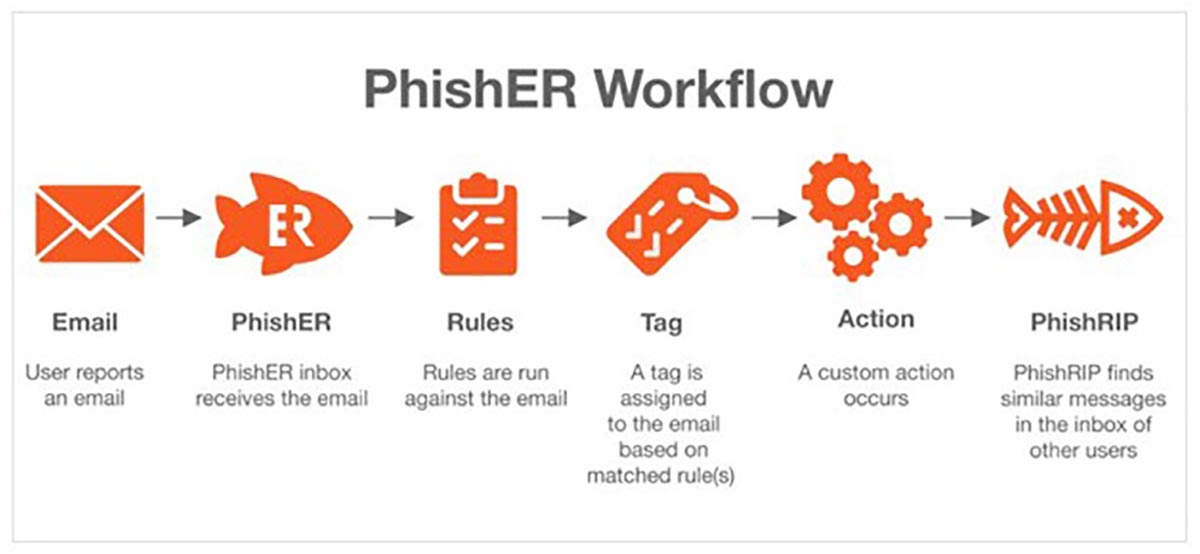
We utilize two tools to help us diagnose malicious emails and keep them out of your inboxes: PhishER and PhishRIP.
What is PhishER?
PhishER is a tool that inspects your reported emails using the phish alert button to determine if they are malicious.
The tool processes the reported emails by grouping and categorizing emails based on rules, tags and actions.
For example, we could make a rule that says look for the word “invoice” in an email and tag it as such if it contains the word.
This allows us to quickly identify the emails that have the word “invoice” to determine if it is a real invoice or a phishing attempt.
We also can make rules based on subject lines, senders, URL domains and more.
Using PhishER is a combination of automated and manual processes. We have automated rules that determine if an email is spam or clean, and the tool automatically tags these emails so we can focus on the potentially dangerous emails.
If an email gets tagged as possible phishing or cannot be categorized based on our rules, then one of our team members will investigate the email to determine if it’s malicious.
“Automated tools such as PhishER and PhishRIP speed up our manual processes so we can spend more time diagnosing potentially malicious emails.”
What is PhishRIP?
Once an email has been deemed a threat, PhishRIP allows us to remove malicious emails from every user’s inbox.
If one person at your organization received a phishing attempt, there’s a good chance others in your organization received the same email or something similar. So, taking it out of everybody’s inbox reduces the chances of a successful phishing attack.
If a client accidentally marks a safe or spam email as phishing, it won’t be taken out of their inbox. They’ll be able to find that email in their deleted items folder.
Only emails we deem as phishing attempts are taken out of inboxes. Remember, spam emails, while annoying, are not malicious. Only phishing emails can hurt your organization.
These automated tools speed up our manual processes so we can spend more time diagnosing potentially malicious emails.
If you have any questions about how the phish alert button works, please reach out to us at support@hungerford.tech.
IT Services Available in West Michigan
Looking to keep your business running smoothly while increasing productivity, security and profitability? Contact us here for all your information technology needs.
Did you like this blog? You can subscribe to our newsletter to receive a weekly email with our latest blog posts.











