What is Quishing and How Do You Protect Yourself?
Editor’s note: In recognition of this October, we are publishing a series of blog posts dedicated to educating and informing you about cybersecurity practices. This is the fourth in a series of posts. Below, you can find a list of links to the rest of the series:
- What is a Pig Butchering Scam and How Do You Protect Yourself?
- 6 Conditional Access Policies You Should Turn on Now
- Tips for Running an Effective Cybersecurity Awareness Campaign
- Early Warning Signs Your Employees Need to Look Out for and Report to IT
- My Dad Lost Thousands of Dollars in a Romance Scam. Here’s How They Work and How to Protect Yourself
- NIST Releases New Password Rules: What Does It Mean for You?
- 7 Reasons Your Organization Needs Cybersecurity Insurance
- Why Does My Organization Need Cybersecurity Insurance and an MSP?
- Top 3 Cybersecurity Threats We Uncovered at GrrCon 2024
- Why Keeping a File with Passwords on Your Computer is a Terrible Idea
- How Do Passwords Get Hacked?
- What Happens When You Use the Phish Alert Button?
- Why Does Social Engineering Happen?
You’ve probably heard of phishing attacks — especially if you’re a regular reader of our other blog posts — and the varieties of phishing attacks, like vishing, HTTPS phishing and smishing.
But have you ever heard of quishing?
Short for QR phishing, quishing is a cybercrime that involves encoding malicious URLs within a seemingly innocent QR code.
Although QR codes have been around since 1994, their popularity has surged in recent years, especially during the COVID-19 pandemic when restaurants needed a hygienic alternative to physical menus and retail stores needed a way for customers to pay without touching cash or pushing buttons on a credit card reader.
How Does a Quishing Scam Work?
Similar to a regular phishing scam, a quishing scam attempts to deceive individuals by taking them to phony websites or automatically downloading malicious software once the QR code is scanned using their phone.
The fake website may ask you to log in to a Microsoft account, which is how attackers steal your credentials. They also set up fake payment portals, so you think you’re paying for a legitimate good or service, but attackers are stealing your credit card information.
Criminals may even cover real QR codes on restaurant tables or street signs with fake stickers that resemble legitimate QR codes to redirect users to harmful websites.
The scam isn’t limited to QR codes you see in public. You may have received an email with a QR code, maybe asking you to verify a purchase or log in to change your password.
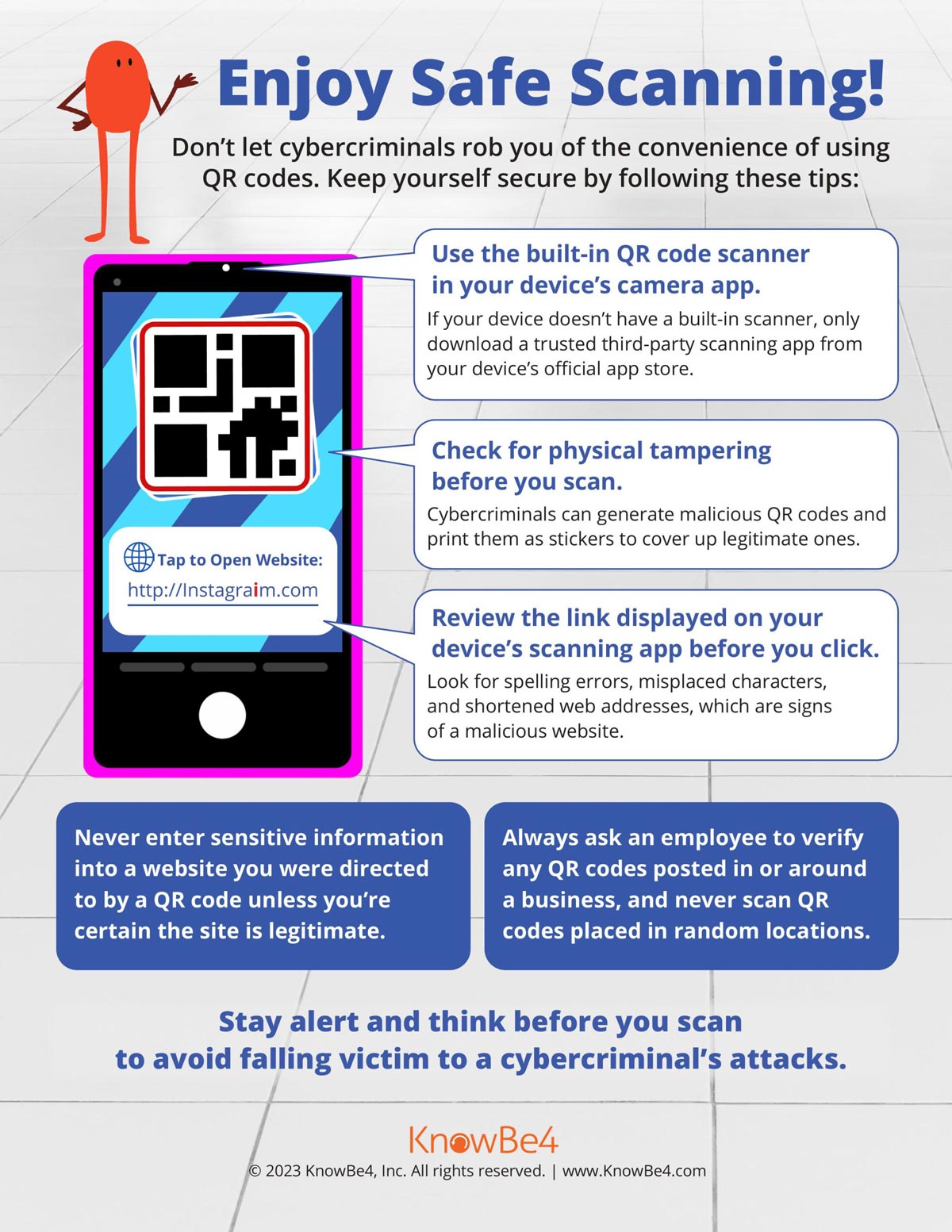
Quishing Scam Warning Signs
Fortunately, a lot of the same advice we offer to avoid phishing scams is the same advice we give to avoid quishing scams.
- If possible, don’t scan QR codes: While a QR code with a URL attached allows you to preview the link before visiting the page, a QR code also could automatically start downloading malicious software the moment it’s scanned. In that case, your personal and organizational data already are compromised.
- Verify the source: Always be cautious when scanning QR codes. Even if you’re getting the code from a legitimate organization, co-worker or friend, you want to ensure the code is authentic. You generally can find the same page if you navigate directly to the organization’s official website.
- Preview the link: Just like with links in suspicious emails, you want to preview the link of the QR code before navigating to the page. If it doesn’t look right, don’t tap the link.
- Be cautious with login screens or personal information: If a scanned QR code takes you to a login page or asks for personal information, it’s a red flag that it could be malicious. Double-check the URL to make sure it’s the organization’s official website. Again, navigate to the page manually to ensure it is real.
- Enable multifactor authentication: If MFA already isn’t enabled, which it should be, the extra layer of security could stop attackers from accessing your account if they steal your credentials. Additionally, don’t accept any MFA requests you didn’t initiate.
While QR codes are a major convenience, attackers exploit this convenience to steal personal and financial information.
If you can avoid scanning them altogether, do so. Otherwise, make sure you do your due diligence before visiting a page linked within a QR code.
Learn More About Phishing Training
Looking to protect your company from quishing scams and other cybersecurity threats? Contact us here to learn how we can help secure your sensitive data.
Did you like this blog? You can subscribe to our newsletter to receive a weekly email with our latest blog posts.











