What is the 3-2-1-1-0 Backup Rule?
IT experts and leading organizations widely endorse the 3-2-1 backup rule because of its straightforward yet effective approach.
As a refresher, you have three total copies of your data, two of which are kept on different platforms to avoid a single point of failure and one of them is stored off-site for additional security against local disasters like fires and floods.
The 3-2-1 backup rule is a great starting point. However, it doesn’t explicitly protect you from ransomware, but there is a variation that does.
“The extra one and zero of 3-2-1-1-0 protect against attacks like ransomware that attempt to encrypt everything it can connect to on your network. Any data stored off-network — like a cloud backup solution — is much less susceptible to getting compromised during a ransomware attack.”
3-2-1-1-0 Goes Even Further than 3-2-1
At Hungerford, we prefer a popular variation of the 3-2-1 rule that builds in additional protection from malware attacks and ongoing testing to increase our confidence that restoring from a backup will work when needed. This is known as the 3-2-1-1-0 rule.
The 3-2-1-1-0 rule is based on the same principles as the 3-2-1 rule, but it goes further:
- 1: Off-network — One of the copies should be off-network, not just off-site.
- 0: Zero Errors — Ongoing monitoring should show zero (0) errors after automated backup testing and recoverability verification.
3-2-1-1-0 Secure Backup Strategy
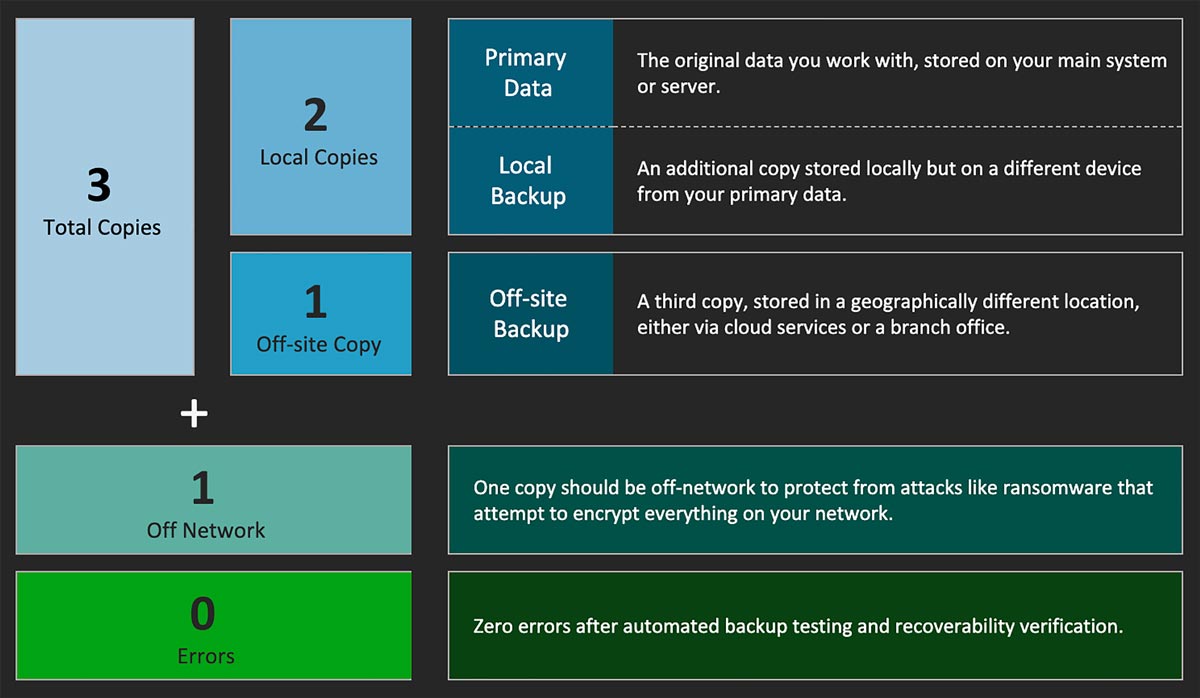
The extra one and zero of 3-2-1-1-0 protect against attacks like ransomware that attempt to encrypt everything it can connect to on your network. Any data stored off-network — like a cloud backup solution — is much less susceptible to getting compromised during a ransomware attack.
Physically separating one copy of your data from the rest of your network is a concept called air gapping, and while it’s not perfect (no security measure is), it greatly decreases the odds of your data being compromised.
A backup that contains errors might fail to restore properly, so it’s important to seek out and resolve errors before the need arises to restore from backups.
Expanded Protection
If you’re looking to expand your protection beyond local and include ransomware, speak with your IT team or managed service provider about the 3-2-1-1-0 backup rule.
It’s a bit more complicated than the 3-2-1 strategy, but that extra 1 and 0 will do wonders if your organization experiences a cyberattack.
West Michigan IT Services
Are you looking to improve backup protocols for your organization? Contact us here to see how we can help keep your business running smoothly while increasing productivity, security and profitability.
Did you like this blog? You can subscribe to our newsletter to receive a weekly email with our latest blog posts.











