Why Does Social Engineering Happen?
Editor’s note: In recognition of this October, we are publishing a series of blog posts dedicated to educating and informing you about cybersecurity practices. This is the 14th in a series of posts. Below, you can find a list of links to the rest of the series:
- What is a Pig Butchering Scam and How Do You Protect Yourself?
- 6 Conditional Access Policies You Should Turn on Now
- Tips for Running an Effective Cybersecurity Awareness Campaign
- What is Quishing and How Do You Protect Yourself?
- Early Warning Signs Your Employees Need to Look Out for and Report to IT
- My Dad Lost Thousands of Dollars in a Romance Scam. Here’s How They Work and How to Protect Yourself
- NIST Releases New Password Rules: What Does It Mean for You?
- 7 Reasons Your Organization Needs Cybersecurity Insurance
- Why Does My Organization Need Cybersecurity Insurance and an MSP?
- Top 3 Cybersecurity Threats We Uncovered at GrrCon 2024
- Why Keeping a File with Passwords on Your Computer is a Terrible Idea
- How Do Passwords Get Hacked?
- What Happens When You Use the Phish Alert Button?
Have you ever seen a post on Facebook from a friend saying, “I’ve been hacked, do not accept any friend requests from me”? This kind of hacking, known as social engineering, involves manipulating, influencing or deceiving someone to gain control over their accounts.
While having your personal social media hacked is scary, the potential impact of a business account being compromised is much more significant.
Social engineering can occur through phone calls, texts, emails or social media to gain unauthorized access.
The Facebook scenario is an example of phishing, a social engineering tactic where the bad actor takes over your account to send messages or friend requests on your behalf. Other types of social engineering include spear phishing and CEO fraud.
“Social engineering is effective because it exploits the human element of security. It’s much easier to trick an employee into revealing sensitive information than to bypass an organization’s technical security measures.”
Social engineering is the opposite of technical engineering, or what is more commonly thought of as hacking. This is where a bad actor uses technical means to bypass an organization’s firewall, install malware or viruses to disrupt a company’s network, or use password guessers to gain unauthorized access.
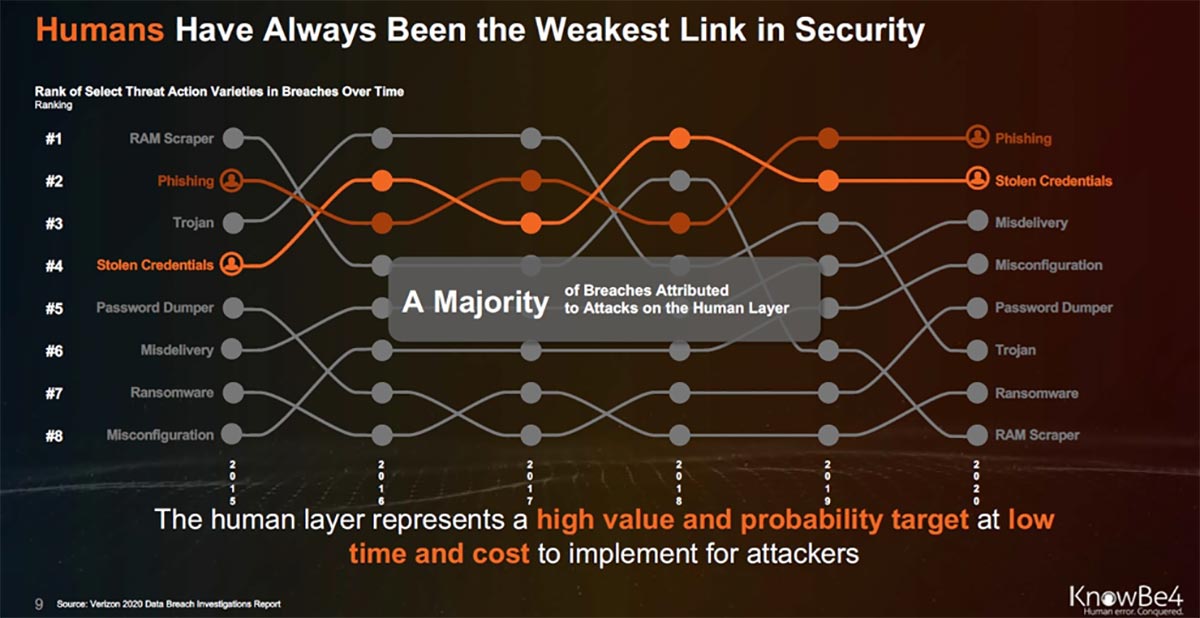
According to PurpleSec, a cybersecurity company, 98% of cyberattacks rely on social engineering as their entry point into an organization’s network.
So why do social engineering tactics make up nearly all cyberattacks?
Path of Least Resistance
Social engineering is effective because it exploits the human element of security. It’s much easier to trick an employee into revealing sensitive information than to bypass an organization’s technical security measures.
Bad actors target the weakest link in an organization’s defense: its people. Their goal is to get the most information with the least resistance.
Consider this: Social engineering involves tricking just one employee into divulging sensitive information. Once the attacker has one foothold, they might use it to reach out to other employees and gain even more information.
This method involves minimal resistance, making it the preferred approach for bad actors.
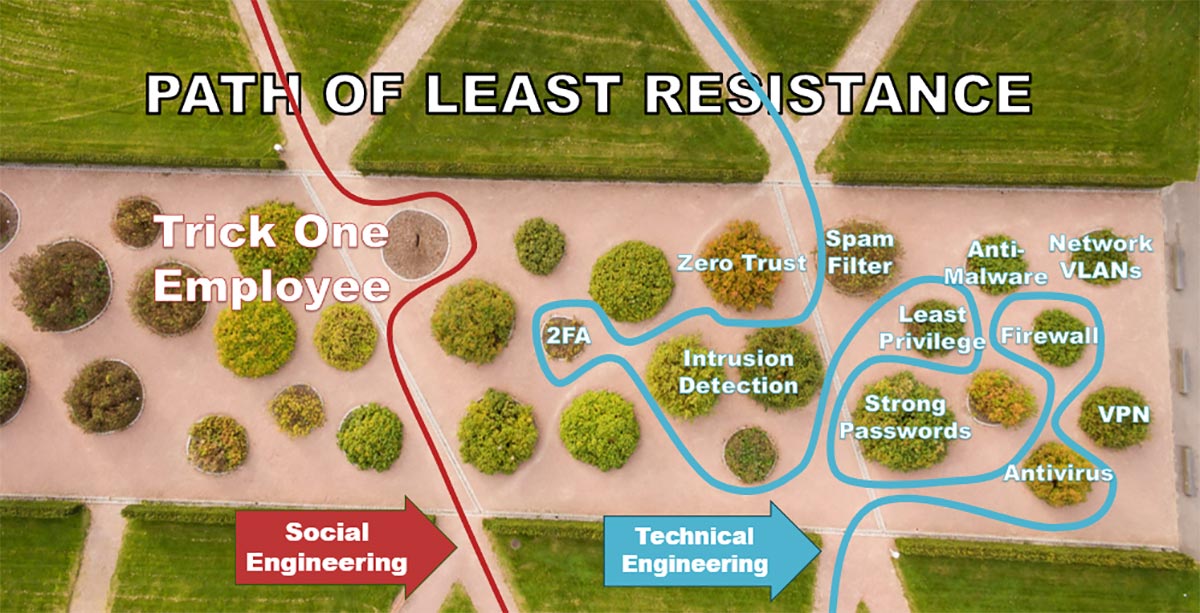
In contrast, technical hacking, which involves breaching firewalls, installing malware or guessing passwords, is more complex and can be thwarted by robust security measures like firewalls, antivirus software, strong passwords and intrusion detection systems.
While these technical breaches can be lucrative for skilled hackers, they are harder to execute because of the technical defenses in place.
However, if an organization lacks these security measures or if they are outdated, technical hacking becomes an easier path. Generally, though, tricking a single, untrained employee is the simplest way to gain unauthorized access.
Tips to Combat Social Engineering Tactics
- Understand social engineering: Recognize that social engineering is a common and effective form of hacking that targets people rather than systems.
- Identify vulnerabilities: Acknowledge that the human element is often the weakest link in your security chain.
- Educate employees: Train your employees to recognize and respond to social engineering attempts.
- Implement robust security: Use firewalls, antivirus software, strong passwords and intrusion detection systems to defend against technical hacking.
- Regular updates: Keep all security measures up to date to protect against evolving threats.
By understanding and addressing these vulnerabilities, you can significantly reduce the risk of social engineering attacks and protect your business from potential harm.
Implement Cybersecurity Measures
Want to improve your organization’s security practices? Contact us here to see how we can help keep your business running smoothly while increasing productivity and profitability.
Did you like this blog? You can subscribe to our newsletter to receive a weekly email with our latest blog posts.











